Enterprise-Grade Compliance, Built In
At Noca, protecting your data is embedded in our architecture and operations. We adopt security-by-design principles, layered technical controls, and independent verification through audits and certifications. This ensures that both regulatory requirements and customer expectations are consistently met with measurable security outcomes.

GDPR
Our systems and processes are architected to meet GDPR requirements through strict data classification, encryption in transit and at rest, role-based access controls, and secure processing environments. We maintain detailed records of data flows and implement privacy impact assessments for new features. International transfers are protected using industry-standard encryption and EU-approved legal mechanisms.

CCPA
We apply CCPA-aligned privacy controls that include transparent data lifecycle documentation, structured logging for data access events, and fine-grained access control at the application and database levels. All customer data is processed in secure, monitored environments, and through automated workflows to ensure timely compliance.

HIPAA
Our platform employs HIPAA-compliant architecture, including encryption of PHI using AES-256, enforced TLS 1.2+ for all network communications, and segregated storage for healthcare-related data. Access to PHI is restricted via least privilege policies, with all access events logged and monitored for anomalies in real time. We execute annual HIPAA risk assessments.

ISO 27001
We maintain an ISO 27001-certified Information Security Management System that enforces control over information assets via documented procedures, continuous risk assessments, and incident response planning. Security controls are validated through internal audits and third-party certification, and metrics are tracked to ensure continuous improvement and alignment with Annex A control objectives.
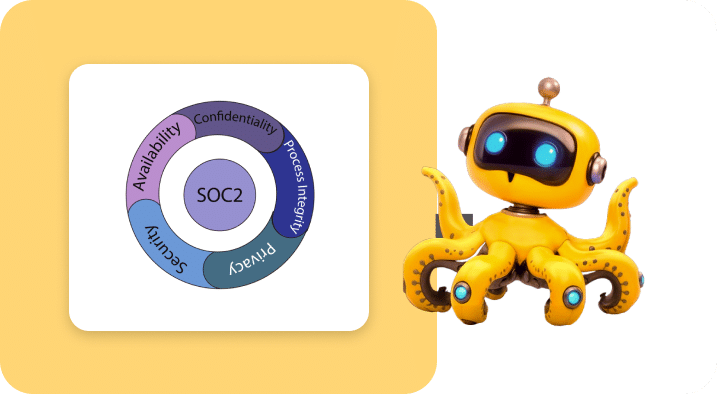
SOC 2
Our SOC 2 Type II controls are mapped to the Trust Services Criteria for
security, availability, and confidentiality. This includes hardened cloud
infrastructure, continuous vulnerability scanning, centralized log
aggregation in AWS CloudWatch, and automated alerting for potential
breaches. Controls are tested throughout the audit period to verify
operational effectiveness.

PCI DSS
Our platform is designed to integrate seamlessly with PCI DSS–compliant
solutions, enabling secure handling of payment and financial transactions.
We follow industry best practices to ensure sensitive financial data is
processed and transmitted safely, minimizing the risk of fraud or
unauthorized access. This integration allows our customers to deliver
trusted, compliant payment experiences while maintaining the highest
standards of security.